The Marine Corps is solving its identity crisis.
No, not who or what a Marine is, but identity as it relates to network management and cybersecurity.
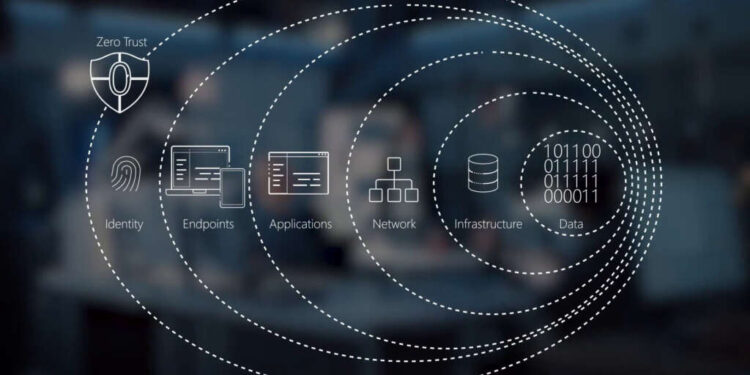
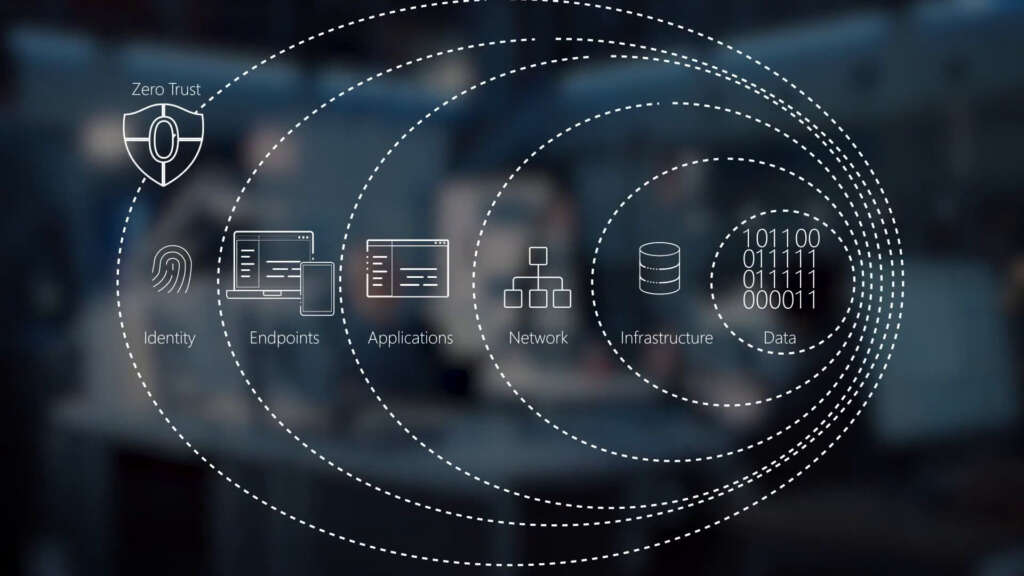
As part of its first major milestone to enable a zero trust architecture, the Marines are deploying a software-defined network (SDN), a software-defined perimeter (SDP), and maybe most importantly, adopting the Naval Identity Service (NIS).
Shery Thomas, the cyber technology officer and technical director for the Marine Corps Information Command, the Marine Corps Forces Cyberspace Command and the Marine Corps Forces Space Command, said all of these support the zero trust principles of network separation and segmentation as the service goes down the path to meet the initial capabilities for zero trust by 2027.
“We expect applications like Marine Online, which is a very application frequently used by Marines for a variety of administrative tasks, to be integrated with NIS by the end of 2024. This partnership across the Department of Navy integrates both the Navy and the Marine Corps into a single identity, credentialing and access management effort that reduces or decreases redundancy and increases security across the board,” Thomas said on Ask the CIO. “It’s a federation of identity for both the Navy and the Marine Corps on whatever platform they’re using it on. Then we’re going to improve upon that across the entire joint service at a higher level. This meets the commandant of the Marine Corps guidance to integrate with the Navy at every level possible and to deliver combat power.”
Through NIS, which the Navy has been developing and testing over the last few years and in May made it an enterprisewide service, the Marine Corps will have a foundational element to address all the pillars of zero trust.
Benefits to mission, customer experience
Thomas said the Marines adoption and integration of NIS, servicemembers and civilians will find the speed at which they access applications will improve dramatically.
“We will have a single sign-on right across the board. You don’t have to go through multiple different factors to get to different applications,” he said. “Multiple applications are federated at the back end, and at the front end in terms of the user, you can do multiple things at the same time. So it improves in terms of mission effectiveness.”
The Marines will start by integrating NIS with back-end administrative systems and then move to warfighting or tactical systems.
Currently, Marines can use single sign-on for some legacy applications both for the warfighter and for administrative tasks, but not all of them. Thomas called the current state not ideal for security or customer experience.
“The first iteration of NIS is with the Navy, and once the Navy is integrated, then we work on joint partners. There are about 35 specific systems that are controlled by one of the other services,” he said. “Can, writ large, Naval forces get on that system and then can somebody from one of the other services get on one of the naval systems or the Marine Corps specific systems? Once you get through each one of these iterations, or each one of these blocks, then we get to a better and better state for the users. Then also we have a heavy consideration on bandwidth in a limited and degraded environment where there’s limited bandwidth for that tactical edge user.”
With NIS being the foundation for many zero trust objectives, Thomas said the Marines, at the same time, are turning to several task groups to help usher the other pieces of the ZTA journey.
Marines to reduce network complexity
The corps set up groups around network and services, around data and artificial intelligence, around cloud services and around workforce talent management.
“We are looking across all of these from the network and services piece it. We’re trying to reduce network redundancy or duplicity of hardware solutions at the tactical edge and the enterprise, and concatenate that to bring it together as much as possible,” Thomas said. “That’s both a fiscally responsible alternative mechanism and it also alleviates the users at the tactical edge in terms of mission relevancy. How are we going about that? I am looking at transport agnostic networks with multiple different pathways for data to go back and forth, and then the last piece of that is when your data centric, you have to make sure the data is secure. It’s not perimeter-level security in terms of the old way of doing business. It is the zero trust mechanism of data centricity.”
Thomas said a key role the Marine Corps Forces Cyberspace Command will play is providing advanced cyber capabilities through automation, security orchestration, automation and response (SOAR) and security information and event management (SIEM).
“The human is not enough and the machine is not enough, but maybe the augmentation of both the machine and user and machine teaming would be the best approach. Now if you multiply the effect of it, then you add with that, not just the machine, but the artificial intelligence on top of the machine with the human, ow you have powers or exponential factors of what we could have done with an individual right at that same time,” he said. “That individual has to have the training and the awareness to use all of these systems and have confidence that the system is providing the right level of things that I need. It has to be curated among individual one versus individual two, who may be using it differently for particular purposes because we all use our devices with different applications to perform certain functions. So those applications or those devices have to be monitored. How are they user, user behavior or what? What are they going after? What am I giving the right level of input back or response back?”
Expanding cloud services
A lot of these automations and cyber capabilities can come from the Marines’ cloud service providers. Thomas said the service, like most organizations, is relying on a multi-cloud, hybrid approach.
“Most people are probably tracking the Joint Warfighting Cloud Computing (JWCC) environment from the DoD side. We are on board with that through the Department of Navy, which has the Neptune program office. We will then distill it down in terms of the Marine Corps,” Thomas said. “We have multiple different applications, multiple different programs of record that are transitioning to the cloud or are in the cloud. Now, how do you figure out the federation of all the different clouds and all the different data in the clouds to have mission relevant decision making and not silo each one of these in terms of, I can only do a warfighting mission in a particular area of responsibility or particular segment, versus having that same individual do an administrative task and also do a task that also requires a different instantiation in that cloud.”
The Marines Corps started with putting certain services in unclassified cloud instances, but are not moving into secret, top secret and beyond options.
Thomas said since the Marines operate in all of these different impact levels, they have to figure out what it means to have multi-level security to ensure the wrong information is not going to the cloud instance.
“We still recognize Marines need to operate at the lowest tactical edge, at the tip of the spear, and be mission relevant. They also need to have that cloud environment for reach back when the network is available,” he said. “The cloud provides a lot of capability in terms of SIEM and SOAR responses, and if you bake that in with the tactical edge and all the cloud providers are looking at the data, then it’s a matter of how do you operate on a cloud both at the tactical edge and have that back and forth reach back?”
Copyright
© 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.