The tenure of a chief information security officer for state governments has seen a significant drop.
A recent survey by the National Association of State CIOs and Deloitte found state CISOs, on average, stayed in their job 23 months, down from 30 months in 2022.
This reduced tenure has long-term effects on the organization from hiring to understanding the state’s culture to staying around long enough to complete projects.
Meredith Ward, the deputy executive director of the National Association of State CIOs (NASCIO), said while each CISO leaves for a different reason, there are some trends including the increased workload and stress of the day-to-day job as well as the opportunity to double or triple their salary in the private sector.
“Our state CISOs are some of the most dedicated public servants that there are, and we see this with our CIOs as well. A lot of them might work a couple of years in the public sector, and then at some point they want to go to the private sector. A lot of times, they will come back to the public sector after several years,” Ward said on Ask the CIO. “I’ve heard some state CIOs say, ‘it can be your first job and your last job.’ A lot of states have increased salaries in the last couple of years. I think that we were a little bit more anxious about what funding might be after COVID, but state budgets were not as bad as we thought. So states have really invested in their employees, so it’s still not going to match the private sector.”
Srini Subramanian, a principal in Deloitte’s Cyber Risk Services practice, said this is why continuity plans and training the next generation of cyber leaders remains so important.
“One of the things that we also say in the call of action is it is important to have succession plans and really groom the next generation leaders within the ranks of the CISO that are ready to take over,” he said. “It is not just at the leadership executive levels; the challenges go all the way to the practitioner levels as well. The cyber talent challenge, or I would call it cyber talent crisis, in state governments is real.”
Fewer CISOs overseeing physical security
This investment in people and salaries also means CISOs are playing a bigger role in their states.
NASCIO and Deloitte, which partnered on the survey to talk to security executives from all 50 states and the District of Columbia, found CISOs say they are providing a range of services, particularly security management and operations (98%); strategy, governance and risk management (98%); and incident response (96%).
The one area where CISOs’ role is contracting is around physical security. NASCIO found 10 fewer CISOs in 2024 than in 2022 say they have responsibility in this area.
“One factor: Only six CISOs report that their states’ cybersecurity budgets cover physical security, down dramatically from 15 in 2022.The trend could also be an indication that states are consolidating data centers and moving to third-party cloud providers,” the survey stated.
Ward said one of the reasons may the continued consolidation and reduction of physical data centers.
Additionally, she said states have reduced their overall physical footprints with more employees working remotely.
Subramanian said as physical and logical systems converge more and more, there is a growing need to integrate these systems, especially around identity and access management provisioning.
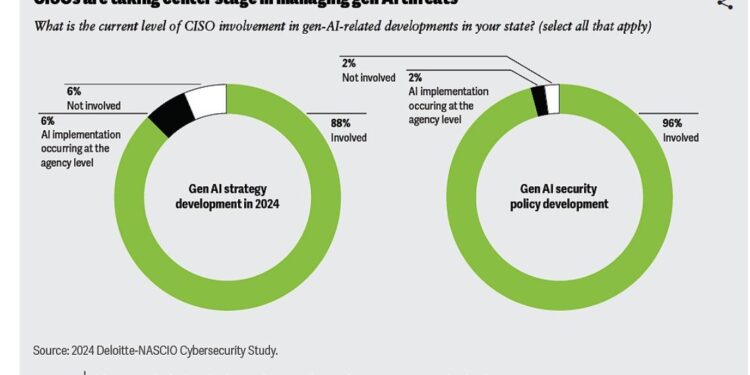
One area where concerns and interest grew was the use of and threat from artificial intelligence.

The survey found 49 of 51 state level CISOs say they are involved in generativeAI security policy development.
“At the state level, CISOs are center stage in managing gen AI threats, with nearly all involved in developing state strategy and security policy and even more expecting future engagement,” the survey stated. “Survey responses indicate that many CISOs are concerned about the unique security risks associated with AI and gen AI. Asked whether their states’ information assets are adequately protected from AI-enabled attacks, all but a handful of CISOs indicated they were only ‘somewhat confident,’ with many reporting ‘not very confident’ or worse.”
At the same time, 21 CISOs say they are already using gen AI to improve security operations, with another 22 planning implementation within the next 12 months.
NASCIO and Deloitte outlined five call to actions for state CISOs based on the survey results.

“We want to make sure that our CISOs can use this. What I know anecdotally from our CISOs is that they will take this and say, ‘all right, how do we line up to what the rest of the country said?’” Ward said. “They’ll use it in their state legislators and say, ‘Look, most states have, XYZ percentage of budget, and we’re down here at this level.’ So it is used as an advocacy tool for them and an education tool. I think that’s really important.”
Subramanian added that the calls to action also can help CISOs figure out how to better make their cases for not only more money, but more collaboration with the business and mission stakeholders.
“There are a couple of things that we are really strongly advocating. One is related to the evolution of cyber threats and how an enterprise identity and access management can improve the posture as well as multi-factor authentication and privilege user management, and doing that consistently across the enterprise will help improve that posture,” he said. “Another key theme was on talent. One of the things we have always seen is states taking an ecosystem approach to tackling the cyber talent challenges. By ecosystem I mean, depending on the partners –private sector partners, and, in some instances, the higher education system–to bring in interns. There even are some examples of a higher education system working with the private sector to do the first level of cyber threat monitoring for the state government. There are those kind of measures that we are encouraging the CISOs and the leaders to look at creative ways of leveraging the ecosystem to improve the cybersecurity measures.”
Copyright
© 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.